dorks eye
DORKS EYE
WHAT ARE GOOGLE DORKS?
Google dorking, also known as Google hacking or Google-fu, is a technique used by individuals to perform advanced and specific searches on the Google search engine to find information that is not typically visible in regular searches. It involves using special search operators and queries to uncover hidden or sensitive data on websites and web applications. Google dorking can be used for various purposes, including:
- Security Testing: Security professionals and ethical hackers use Google dorking to discover vulnerabilities and weaknesses in websites and web applications. By crafting specific queries, they can find exposed login pages, sensitive directories, error messages that reveal system information, and more.
- Information Gathering: Cybercriminals or malicious actors may also use Google dorking to find targets for cyberattacks. They can search for email addresses, passwords, and other confidential information that may have been inadvertently exposed online.
- Competitive Intelligence: Businesses and marketers can use Google dorking to gather information about their competitors. This might include identifying specific product listings, customer reviews, or pricing information that is not readily accessible through standard searches.
- Research: Researchers and journalists may employ Google dorking to uncover publicly available data that is not easily found through traditional search methods. This can include academic papers, government documents, and more.
CHARACTERISTICS:
- Python3-Based: Dorks Eye is developed in the Python3 programming language, making it accessible and easy to use on various platforms.
- Google Dorks: It specializes in utilizing Google Dorks, which are advanced search queries, to identify vulnerable links on the internet.
- Link Gathering: The tool gathers links to web pages and applications from the internet. These links can potentially lead to websites with security vulnerabilities.
- Sensitive Data Discovery: Dorks Eye is capable of revealing sensitive information, including SQL queries, usernames, passwords, bank details, and more. This functionality is crucial for security testing and auditing.
- Results Export: It supports saving the results in a text-formatted file. This feature enables users to document and analyze the discovered information.
- Open Source: Dorks Eye is an open-source tool, which means it is freely available for anyone to use and modify. It is hosted on GitHub, allowing for community contributions and updates.
- Security Testing: One of its primary use cases is security testing and vulnerability assessment, helping security professionals and ethical hackers identify potential weaknesses in websites and applications.
INSTALLATION OF EYE DORKS:
- Step1: Dorks Eye require python to run. Check if the python is installed on your kali or not. To check run the following command.
- python –version
- Step2: Utilize the provided command to perform the installation of the tool on your Kali Linux operating system.
- git clone https://github.com/BullsEye0/dorks-eye.git
- Step3: Now, execute the following command to navigate to the tool's directory. You need to be inside this directory to run the tool.
- cd dorks-eye
- Step4: While inside the "dorks-eye" directory, you'll need to install a dependency for dorks-eye using the following command.
- sudo pip3 install -r requirements.txt
- Step5: Once all the dependencies has been installed run the following command to run the tool.
- python3 dorks-eye.py
WORKING WITH DORK EYE ON KALI LINUX OS:
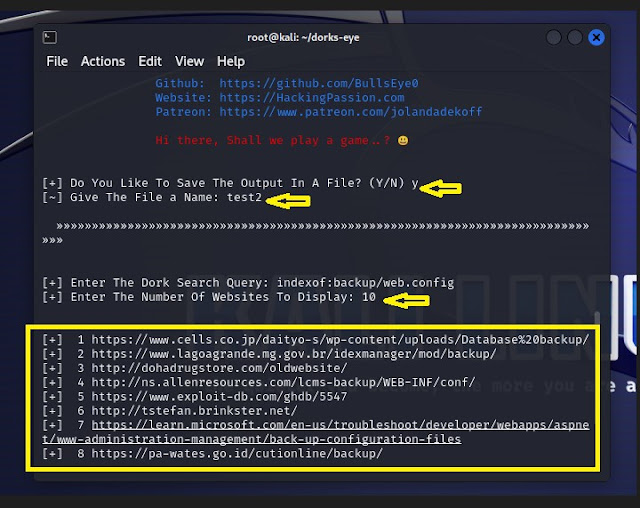
USAGE: TO FIND CONFIG FILES
- Step1: Run the following command to start the tool
- python3 dorks-eye.py
- Step2: Given below query will give the list of links of vulnerable websites.
- indexof:backup/web.config
- Step3: We will be showcasing more than 10 vulnerable sites on the terminal, although we can display additional websites as well.
- Step4: Upon visiting the link, we have accessed the contents of the "conf" directory, which comprises of many different files.














Comments
Post a Comment