Process Hacker
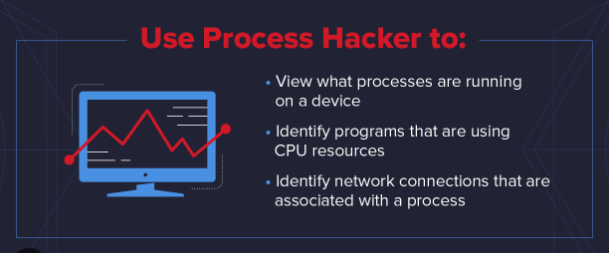
Process Hacker What is Process Hacker? Process Hacker is an open-source system monitoring utility and task manager for Microsoft Windows. It serves as an advanced alternative to the native Windows Task Manager, providing users with a more comprehensive set of features and functionalities. The primary purpose of Process Hacker is to offer detailed insights into the processes running on a Windows system, allowing users to monitor resource usage, manage services, and troubleshoot issues. Unlike the standard Task Manager, Process Hacker offers a wealth of additional information, including detailed process properties, network connections, and system resource utilization. Users can delve deep into the inner workings of their system, making it a valuable tool for both advanced users and system administrators. Additionally, Process Hacker allows users to manipulate and terminate processes, services, and network connections, providing a higher level of control over system activities. ...