Comprehensive Guide to Using JADX for APK Analysis
Guide to Using JADX for APK Analysis
JADX (Java Decompiler) is an open-source tool that allows you to decompile APK files into readable Java code. This is an essential tool for Android app pentesting, helping you inspect the app's source code for vulnerabilities like hardcoded credentials, API keys, insecure configurations, and logic flaws.
Here’s a complete guide:
Step 1: Download and Install JADX
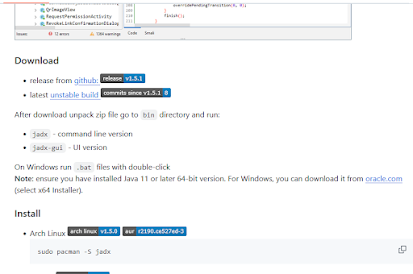
Download JADX:
- Visit the official repository: https://github.com/skylot/jadx.
- Download the latest release as a ZIP file from the Releases section (look for
jadx-release.zip). 
Extract the ZIP File:
- Extract the downloaded ZIP file into a folder on your system.
3. Run JADX GUI:
- Navigate to the extracted folder.
- Double-click on
jadx-gui.bat(on Windows) to launch the GUI. - If using a terminal, navigate to the JADX directory and run:



Comments
Post a Comment