REGRIPPER (FORENSIC TOOL)
RegRipper
What is RegRipper?
RegRipper is a tool used in digital forensics and incident response for extracting valuable information from Windows Registry hives. The Windows Registry is a hierarchical database that stores configuration settings and options on Microsoft Windows operating systems. It contains a wealth of information about user activities, system settings, installed software, network configurations, and more. Digital forensic analysts and cybersecurity professionals use RegRipper to streamline the process of analyzing Windows systems for evidence of malicious activities, user actions, and system configurations. By examining the extracted data, investigators can better understand what actions have taken place on the system, identify potential security breaches, and gather evidence for legal proceedings if necessary.
It's important to note that while RegRipper can be a valuable tool in the realm of digital forensics, it requires careful usage and interpretation of the extracted data to avoid misinterpretation or drawing incorrect conclusions. It's always recommended to have a solid understanding of the Windows Registry structure and the context of the system being analyzed.
What is the use of Regriper tool?
The main use of the RegRipper tool is to assist in digital forensics and incident response by automating the extraction of valuable information from Windows Registry hives. The Windows Registry is a database in Windows operating systems that stores configuration settings, user activities, software installations, and various system-related data. The RegRipper tool helps forensic analysts and investigators to:
- Extract Evidence: RegRipper aids in extracting relevant data from Registry hives, providing insights into user actions, system configurations, installed software, and network settings.
- Investigate Incidents: By analyzing Registry data, RegRipper can help investigators understand the history of activities on a system, potentially identifying signs of malicious behavior or security breaches.
- Automate Analysis: The tool offers a set of predefined plugins, each targeting specific Registry keys and values, automating the process of data extraction and reducing manual effort.
- Efficient Analysis: RegRipper's automation allows for quicker analysis of Registry data compared to manually searching through the Registry hives.
- Pattern Recognition: The tool's plugins are designed to recognize patterns and extract relevant information, such as user login times, executed programs, and recently accessed files.
- Support Legal Cases: Extracted data can be used as evidence in legal proceedings, providing a detailed record of system activities.
- Comprehensive Insights: RegRipper covers a wide range of Registry areas, providing insights into user behavior, system settings, and potential security issues.
- Consistency: The tool provides a standardized way of extracting data, enhancing the consistency and reliability of forensic analysis.
It's important to note that while RegRipper is a valuable tool, proper training and understanding of the Windows Registry structure, as well as the interpretation of the extracted data, are crucial to ensure accurate and meaningful results.
Steps to install this tool:
Step1:-Visit the GitHub Repository through the link provided below.
LINK:- https://github.com/keydet89/RegRipper3.0
Step2:-Click on the green "Code" button, and then select "Download ZIP" from the dropdown menu.
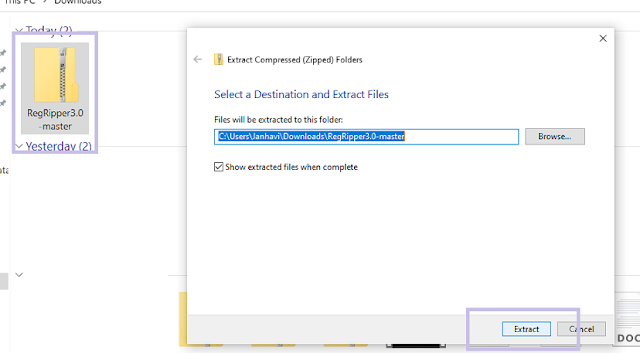
Step3:-Once the ZIP file is downloaded, extract its contents to a directory of your choice on your Windows machine.
Remember that using digital forensic tools like RegRipper requires knowledge and responsibility, as analyzing and interpreting the extracted data accurately is crucial for effective investigation.






Comments
Post a Comment