NETWORK MINER (FORENSIC TOOL)
Network Miner
What is Network Miner ?
Network Miner is a sophisticated and invaluable software tool utilized within the realm of network analysis and cybersecurity. It serves as a fundamental asset for professionals and researchers in the fields of network management, digital forensics, and intrusion detection. With its capabilities deeply rooted in the examination of network traffic, Network Miner plays a pivotal role in capturing, scrutinizing, and comprehending the intricate interactions occurring within network packets. Its significance extends to deciphering vital information embedded within these packets, such as IP addresses, hostnames, domains, files, and more. By facilitating the extraction of such data, it empowers experts to uncover hidden patterns, identify potential security breaches, and expose vulnerabilities within network infrastructure. Moreover, Network Miner aids in the extraction and reassembly of files and images transmitted across networks, thereby assisting in the contextual understanding of network activity. Its graphical interface further simplifies the navigation through captured data, enhancing the user experience and enabling more efficient analysis. In essence, Network Miner serves as an indispensable instrument for dissecting network intricacies, fortifying cybersecurity measures, and contributing to a deeper comprehension of digital communication within modern computer networks.
What are the features of Network Miner?
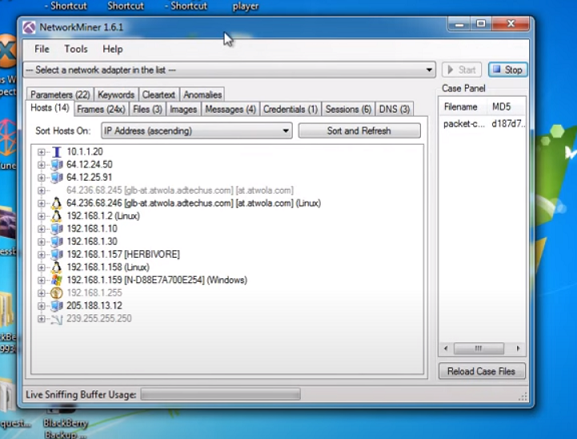
- Packet Capture and Analysis: Network Miner allows users to capture network packets from live interfaces or saved PCAP files. It then automatically analyzes these packets to extract information about the communication within the network. This feature is crucial for understanding the flow of data and interactions between different hosts.
- Automated Data Extraction: The tool automates the process of extracting valuable information from network packets. It identifies and presents details such as IP addresses, hostnames, MAC addresses, and more. This automated extraction accelerates the analysis process and provides insights into the network's structure.
- File Extraction: Network Miner is equipped to detect and extract files that are being transferred over the network. This capability is vital for cybersecurity professionals who need to identify potential malware or unauthorized file transfers. The extracted files can be further analyzed to determine their nature and intent.
- Image Reassembly: In scenarios where images are transmitted in a fragmented manner across the network, Network Miner can reassemble these fragments to display the complete image. This visual representation can offer insights into the content being exchanged, aiding in investigations.
- Keyword Search: The keyword search feature enables users to search for specific terms, URLs, or patterns within the captured network traffic. This is particularly useful for pinpointing relevant data related to specific incidents or suspicious activities.
- Metadata Extraction: Network Miner can extract metadata from various network protocols. This includes details like protocol version, headers, and other contextual information. This metadata can provide valuable context for understanding the nature of the network communication.
- DNS Analysis: With its DNS analysis capabilities, Network Miner can reveal domain names and their associated IP addresses that are being accessed or queried within the network. This is important for identifying potential connections to malicious domains.
- User-Friendly Interface: Network Miner offers a user-friendly graphical interface that simplifies the navigation and interpretation of captured data. This makes it accessible to both experienced network analysts and those new to network forensics.
- Data Export: The tool allows users to export the extracted data, files, and images for further analysis using other tools. This feature facilitates collaboration and enables in-depth investigations that might require a combination of different software.
These features collectively empower cybersecurity professionals, network administrators, and digital forensics experts to effectively monitor, analyze, and secure network traffic, making Network Miner an invaluable asset in maintaining a secure and well-functioning network environment.
Steps to download and install this tool:-
Step1:-Proceed to the given link and then select "NetworkMiner".
LINK:-https://www.netresec.com/?page=NetworkMiner










Comments
Post a Comment