OWASP Mobile Top 10
What is Mobile OWASP?
OWASP mobile is a set of guidelines and best practices for securing mobile applications. It includes the Mobile Application Security Verification Standard (MASVS), the OWASP Top 10 Mobile Risks, and other resources.
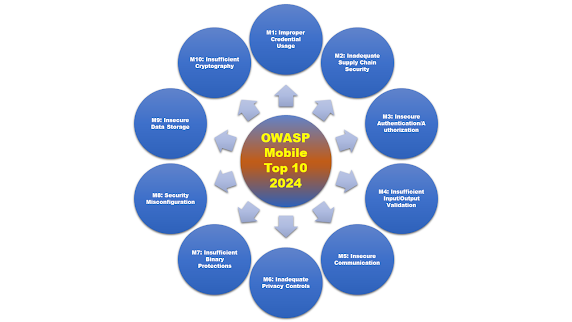
OWASP Mobile Top 10 Risks for 2024:
1. Improper Credential Usage – Storing, transmitting, or managing credentials insecurely, leading to unauthorized access.
2. Inadequate Supply Chain Security – Using third-party components with vulnerabilities, leading to security risks.
3. Insecure Authentication/Authorization – Weak authentication mechanisms allowing attackers to bypass login or access controls.
4. Insufficient Input/Output Validation – Failing to validate or sanitize user input, making the app vulnerable to injection attacks.
5. Insecure Communication – Not properly encrypting or securing data transmitted between the app and servers, leading to data interception risks.
6. Inadequate Privacy Controls – Improper handling of user data, leading to unauthorized data access, exposure, or regulatory violations.
7. Insufficient Binary Protections – Weaknesses in code obfuscation, encryption, or anti-tampering mechanisms, allowing attackers to reverse-engineer or manipulate the app.
8. Security Misconfiguration – Poor security settings or missing configurations that expose the app to attacks.
9. Insufficient Logging and Monitoring – Failing to detect or respond to security incidents due to inadequate logging or monitoring.
10. Outdated or Insecure Components – Using old, vulnerable, or unsupported libraries, frameworks, or APIs, leading to potential exploits.
CONCLUSION
The OWASP Mobile Top 10 for 2024 highlights key security risks in mobile apps, including insecure authentication, data protection flaws, supply chain vulnerabilities, and outdated components. It emphasizes the need for strong encryption, secure coding, and binary protections. Developers can mitigate these risks through secure frameworks, regular testing, and continuous monitoring to safeguard user data and prevent cyber threats.
.png)


Comments
Post a Comment