DNS CACHE POISONING
DNS CACHE POISONING IN KALI
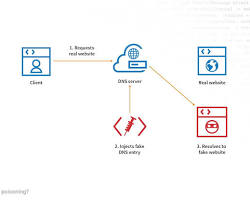
WHAT IS DNS CACHE POISONING?
DNS cache poisoning, also known as DNS spoofing, is a cyberattack where malicious actors corrupt the DNS cache of a server or client. This manipulation causes DNS queries to return incorrect responses, redirecting users to fraudulent or malicious websites instead of the intended legitimate ones.
1. COMPROMISING THE DNS RESOLVER:
Attackers exploit vulnerabilities in DNS resolvers (servers that translate domain names into IP addresses) to inject false DNS records.
2. REDIRECTING TRAFFIC:
When a user attempts to access a legitimate website, the compromised DNS resolver provides the fake IP address stored in its cache.
3. DATA THEFT:
Phishing sites aim to steal usernames, passwords, credit card information, and other sensitive data.
4. USER MISDIRECTION:
This redirects the user to a malicious website designed to:
Steal login credentials (phishing)
Download malware onto the user's device
Deliver other harmful content
5. REPUTATIONAL DAMAGE:
Businesses can suffer reputational damage if their customers are redirected to malicious sites.
PREVENTION AND MITIGATION:
1. STRONG DNS SERVER CONFIGURATION:
Implementing security measures like access control lists (ACLs) and rate limiting can help prevent unauthorized access to DNS servers.
2. REGULAR SOFTWARE UPDATES:
Keeping DNS software and operating systems up-to-date with the latest security patches is crucial.
3. USE SECURE DNS SERVICES:
Consider using public DNS services like Google Public DNS or Cloudflare DNS, which often have built-in security measures.
CONCLUSION:
DNS cache poisoning is a serious threat, and it's essential to implement appropriate security measures to protect your systems and users from these attacks. The focus should always be on enhancing security and protecting systems from malicious attacks.




Comments
Post a Comment