Netsparker: web application security scanner
Netsparker
What is Netsparker?

Netsparker is a powerful web application security scanner that plays a crucial role in ensuring the safety and integrity of online platforms. Developed by Netsparker Ltd., it is specifically designed to automate the process of identifying security vulnerabilities within web applications. In essence, Netsparker acts as a virtual cybersecurity expert, tirelessly scanning websites, web applications, and web services to pinpoint potential weaknesses that malicious hackers could exploit.
What sets Netsparker apart is its advanced automation technology, which allows it to efficiently crawl through complex web applications, analyze their structures, and simulate real-world hacking techniques to discover vulnerabilities. These vulnerabilities can range from common issues like SQL injection and cross-site scripting (XSS) to more intricate security flaws. Once identified, Netsparker provides detailed reports, aiding developers and security teams in understanding the vulnerabilities' nature and severity.
Netsparker's user-friendly interface and accurate scanning capabilities make it an indispensable tool for businesses and organizations seeking to fortify their online presence. By identifying and addressing vulnerabilities proactively, Netsparker assists in safeguarding sensitive data, maintaining user trust, and ensuring compliance with security standards and regulations. As the digital landscape continues to evolve, Netsparker remains a vital asset in the ongoing battle against cyber threats, allowing businesses to stay one step ahead of potential attackers and protect their digital assets effectively.
What are the features of this tool?
Netsparker is a comprehensive web application security scanner that offers a range of features to help businesses identify and address security vulnerabilities effectively. Here are some key features of Netsparker:
- Accurate Vulnerability Detection: Netsparker employs advanced scanning technology to accurately detect a wide array of web application vulnerabilities, including SQL injection, cross-site scripting (XSS), remote file inclusion, and more. Its automated approach ensures thorough coverage of the application's security landscape.
- Proof-Based Scanning: Netsparker doesn't just identify vulnerabilities; it also provides proof of exploit, allowing developers to understand the context and the potential impact of each vulnerability. This proof-based scanning approach enhances the credibility of the identified issues.
- Automatic Crawling and Scanning: Netsparker automates the process of crawling and scanning websites and web applications. It navigates through complex structures, authenticates where necessary, and scans dynamically generated content, ensuring comprehensive coverage of the target application.
- REST API Security Testing: Netsparker can test the security of RESTful APIs, which are widely used for web and mobile applications. It identifies vulnerabilities specific to API endpoints, ensuring that the entire web ecosystem is secure.
- Integration Capabilities: Netsparker integrates seamlessly with various development and issue tracking tools like JIRA, GitHub, and Jenkins. This integration streamlines the vulnerability remediation process, allowing development teams to address issues promptly.
- Compliance and Reporting: Netsparker helps organizations comply with industry standards and regulations such as OWASP Top Ten, PCI DSS, and HIPAA. It generates detailed reports that provide an overview of the security posture, making it easier for businesses to demonstrate compliance to auditors and stakeholders.
- Scan Policy Customization: Netsparker allows users to customize scan policies based on specific requirements. Customization options include authentication settings, URL rewriting rules, and content exclusion parameters, ensuring tailored and efficient scanning for individual applications.
- Vulnerability Management: Netsparker provides a centralized platform for managing identified vulnerabilities. It categorizes issues based on severity, highlights critical problems, and offers guidance on remediation, empowering development teams to prioritize and address security concerns effectively.
- Scalability: Netsparker is designed to handle large-scale scanning requirements. It can scan multiple web applications simultaneously, making it suitable for enterprises with diverse and extensive digital footprints.
Common options that are typically available in web application security scanners Netsparker:
- URL Targeting: Users can specify the target web application's URL or a range of URLs to scan. This allows Netsparker to focus its scanning efforts on specific parts of a website or particular web applications.
- Authentication Configuration: Netsparker often allows users to configure authentication settings if the target application requires login credentials. This ensures the scanner can access restricted areas of the application during the scan.
- Scan Policies: Users can customize scanning parameters based on the specific needs of their application. This might include specifying the types of vulnerabilities to scan for, the depth of the scan, or excluding certain parts of the website from the scan.
- Crawling Options: Netsparker typically provides options related to how the scanner navigates through the website. This includes settings for handling JavaScript-based navigation, handling session management, and managing complex authentication mechanisms.
- Vulnerability Reporting: The tool allows users to generate detailed reports after the scan is complete. Reports often include information about discovered vulnerabilities, including proof of exploit, severity level, and recommendations for remediation.
- Integrations: Netsparker can integrate with various development and project management tools. This allows for seamless communication of scan results with development teams, enabling efficient vulnerability remediation workflows.
- Compliance Checks: Netsparker might offer specific checks tailored to compliance standards such as OWASP Top Ten, PCI DSS, or HIPAA. These checks ensure that the scanned applications meet specific security compliance requirements.
- REST API Testing: Modern web applications often rely on REST APIs. Netsparker can include features to specifically test the security of these APIs, identifying vulnerabilities in the API endpoints.
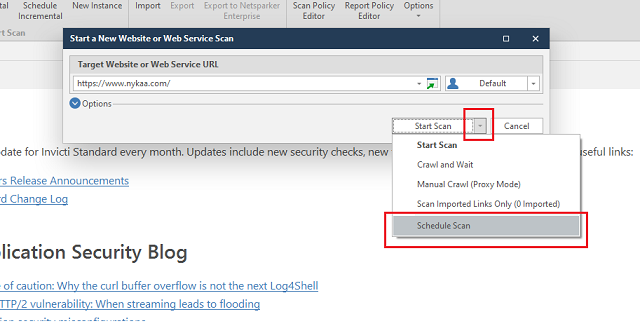
- Scheduler: Some versions of Netsparker provide the option to schedule scans at specific times. This automated scheduling ensures regular security checks without manual intervention.
- Interactive Testing: Some advanced scanners like Netsparker offer interactive scanning where security professionals can manually explore the application while the tool records the interactions. This can be particularly useful for finding complex security issues.
Steps to install and use this tool:-
Step1:- Download the software and click on "Open" to initiate the installation process. Click on " Install".
Step2:- Click "Next".
 |
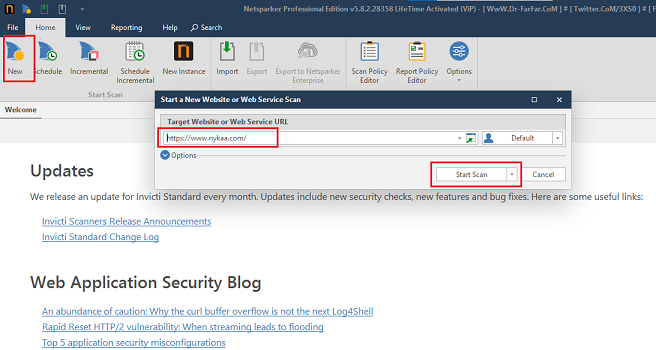
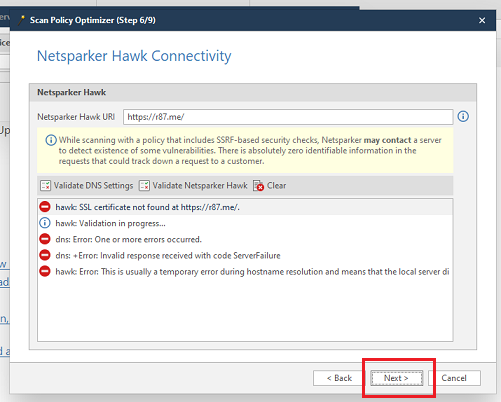
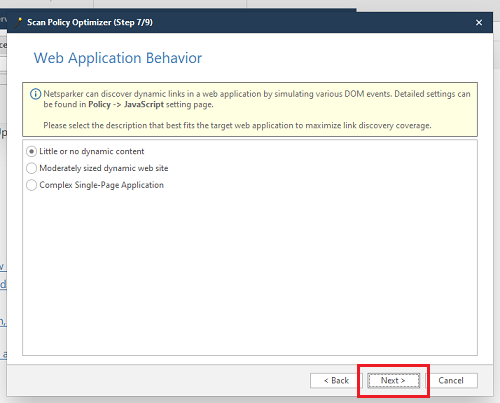
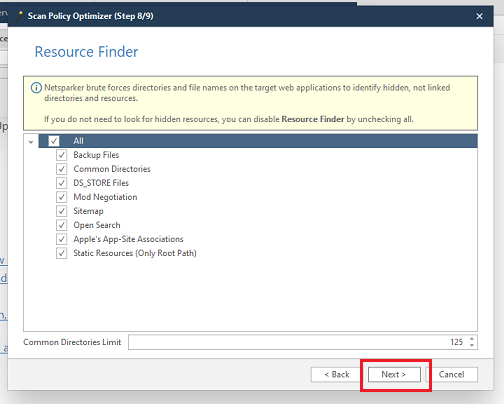
Step6:- Click on "New", pate the link you desire to scan and then click on "Start Scan".
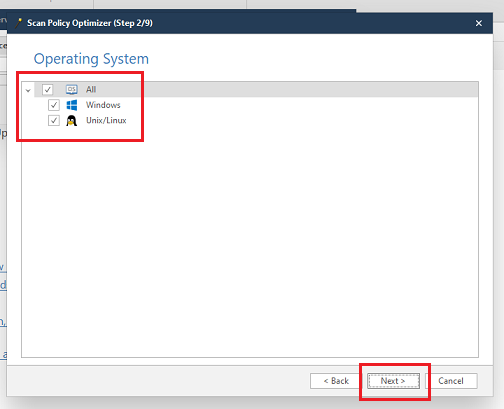
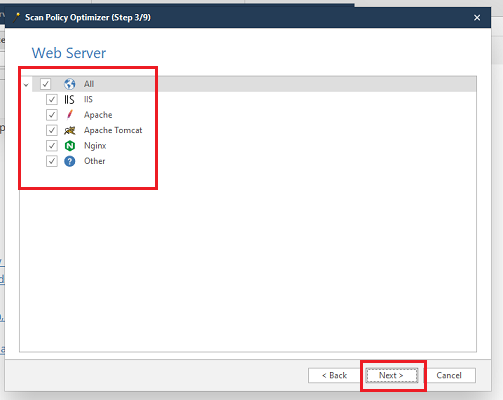
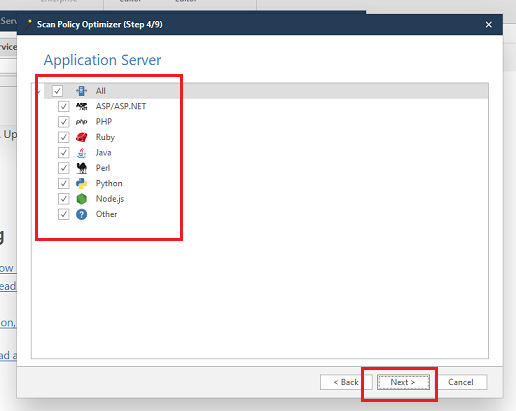
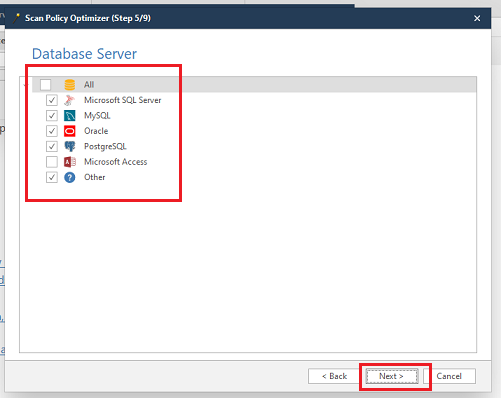





Comments
Post a Comment