Nmap: network scanning tool
Nmap
What is Nmap?

Nmap, short for Network Mapper, is a versatile and powerful open-source network scanning and discovery tool that plays a crucial role in network security and administration. It was developed by Gordon Lyon (also known as Fyodor) and is widely used by network administrators, security professionals, penetration testers, and system administrators. Nmap's primary purpose is to help users understand and evaluate the security and health of their network infrastructure. Nmap works by sending specially crafted packets to target hosts and analyzing the responses it receives. These responses help determine which hosts are active on a network, identify the services or daemons running on those hosts, and pinpoint open ports that may serve as potential entry points for unauthorized access or attacks. Nmap's core functionality is centered around scanning techniques, including TCP, UDP, and ICMP scans, allowing users to gather valuable information about the network.
One of Nmap's distinguishing features is its flexibility and extensibility. It offers a wide array of scanning options and techniques to adapt to various network environments and requirements. Users can customize their scans to be aggressive or stealthy, depending on their objectives. Nmap also provides a scripting engine, known as NSE (Nmap Scripting Engine), which enables users to create custom scripts to interact with target hosts and perform various security-related tasks. Beyond its fundamental port scanning capabilities, Nmap offers advanced features like OS detection, service version detection, and the ability to perform host discovery, network topology mapping, and vulnerability assessment. It provides valuable insights into the network's structure, security posture, and potential weaknesses.
While Nmap is an essential tool for network and system administrators, it should be used responsibly and with proper authorization. Unauthorized or aggressive scanning can disrupt networks and may have legal and ethical implications. Therefore, it is vital to adhere to ethical standards and always obtain permission before scanning or probing a network, especially if it is not your own. Nmap is a valuable resource for those tasked with securing and managing network infrastructure, but it should be employed in a responsible and lawful manner to protect network integrity and privacy.
What are the features of this tool?
Nmap (Network Mapper) is a versatile and feature-rich network scanning and discovery tool with a wide range of capabilities. Some of its key features include:
- Port Scanning: Nmap excels at scanning and identifying open ports on target systems. It can perform a variety of scan types, including TCP, UDP, and ICMP scans, to discover which ports are actively listening on a host.
- Service and Version Detection: Nmap can determine the services and applications running on open ports, along with their version information. This feature is valuable for understanding the software stack on target systems.
- OS Detection: Nmap can attempt to identify the operating system of the target host based on various characteristics of its responses to Nmap probes. This information helps in profiling the target network.
- Scripting Engine (NSE): Nmap includes a scripting engine that allows users to create custom scripts to interact with target hosts. NSE scripts can be used for various tasks, including vulnerability assessment, network discovery, and automation.
- Host Discovery: Nmap can be used to discover hosts on a network, both for local and remote networks, even if they are hidden behind firewalls or routers. It can perform various discovery techniques, such as ARP scans, ICMP scans, and DNS resolution.
- Network Topology Mapping: Nmap can create network topology maps, showing how hosts are interconnected. This is particularly useful for network administrators and security professionals.
- Aggressive and Stealth Scanning: Nmap offers a range of scanning options, from aggressive scans that are more likely to be detected, to stealthy scans designed to evade intrusion detection systems.
- Customization: Nmap is highly configurable, allowing users to fine-tune scan parameters, customize probe packets, and adjust timeouts and thresholds to meet their specific needs.
- Output Formats: Nmap can produce scan results in various output formats, including plain text, XML, and even interactive graphical reports. This makes it suitable for different use cases and integration with other tools.
- Cross-Platform: Nmap is available for various operating systems, including Linux, Windows, macOS, and more. It can be installed and used on a wide range of platforms.
- Scripting Community: Nmap has an active scripting community that continually develops and shares NSE scripts, expanding the tool's capabilities and making it adaptable to various security and network assessment tasks.
- Open Source: Nmap is open-source software, which means it's freely available and its source code is open for review and customization.
Nmap's rich feature set, along with its flexibility and extensibility, makes it a go-to tool for network administrators, security professionals, and penetration testers for network discovery, security assessment, and troubleshooting. However, it's important to use Nmap responsibly and with proper authorization to avoid any potential legal or ethical issues.
Steps to install and use Nmap:-
Step1:- Open a terminal in Kali Linux.Upgrade & Update the package repository using the following command: "sudo apt update, sudo apt upgarde".

Step2:- You can now install Nmap using the following command: "sudo apt install nmap".

Step3:- You need to know the ip address of the target device, for the scan, if you don't know it you can fing it using the following command: "ifconfig".

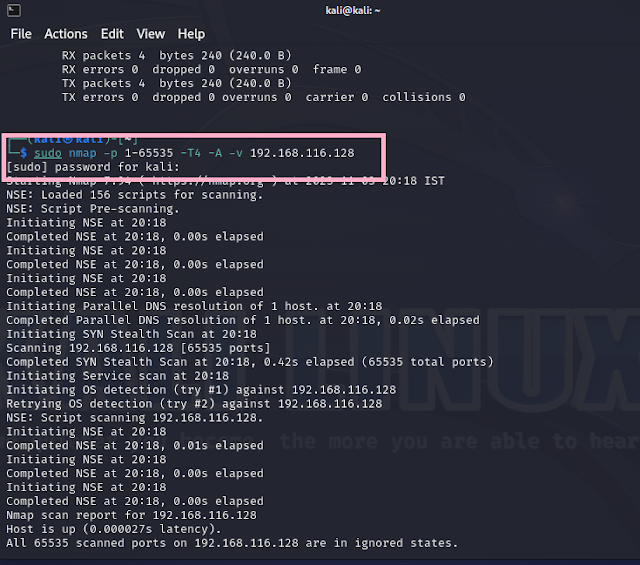
Step4:- Use the nmap command to perform a simple TCP scan. Replace <target> with the IP address or hostname of the system you want to scan.
Command: "sudo nmap -p 1-65535 -T4 -A -v <target>".
-p 1-65535: This option specifies the range of ports to scan (all 65535 in this case).
-T4: This option sets the timing template to "aggressive" to speed up the scan.
-A: This option enables OS detection, version detection, script scanning, and traceroute.
-v: This option enables verbose output so you can see the scan progress.



Comments
Post a Comment