Introduce to HTML Injection ?
HTML Injection, also known as cross-site scripting (XSS), is a web vulnerability where an attacker injects malicious HTML or script code into a web application's input fields, URLs, or other user-controlled data. When the application does not properly sanitize or validate this input, it is displayed on web pages without proper encoding or filtering. As a result, unsuspecting users who view the affected pages may have the injected code executed by their browsers, leading to client-side attacks, data theft, session hijacking, or other malicious activities. Proper input validation and output encoding are crucial to mitigate the risk of HTML Injection vulnerabilities.
What is Reflected HTML Injection ?
Reflected HTML Injection, also known as Reflected XSS (Cross-Site Scripting), is a type of security vulnerability that occurs when untrusted data from a user's input is embedded into an HTML response without proper sanitization or encoding. This vulnerability allows an attacker to inject and execute malicious code within the victim's browser.
The consequences of a successful reflected HTML injection attack can vary depending on the attacker's intent. It can lead to session hijacking, cookie theft, defacement of websites, phishing attacks, or the distribution of malware.
Why is dangerous Reflected HTML Injection ?
This vulnerability allows an attacker to execute arbitrary code within the victim's browser. By injecting malicious scripts, the attacker can manipulate the victim's browsing experience, steal sensitive information, or perform unauthorized actions on behalf of the victim.
Reflected HTML Injection can be used to steal session cookies, which are used to authenticate and identify users. By obtaining a victim's session cookie, an attacker can impersonate the user and gain unauthorized access to their accounts.
Attackers can leverage reflected HTML injection to craft convincing phishing attacks. They can create malicious links that appear legitimate, tricking users into clicking them and disclosing sensitive information, such as login credentials or financial details.
If a website or application is vulnerable to reflected HTML injection attacks, it can negatively impact the trust and confidence users have in the organization. Customers may lose faith in the security measures in place and be reluctant to engage or transact with the affected entity.
Mitigation :
Implement thorough input validation on the server side. Validate and sanitize all user-supplied input to ensure it meets the expected format, length, and data type. Reject or sanitize any input that contains potentially malicious characters or scripts.
Implement a Content Security Policy that restricts the sources from which scripts, stylesheets, and other resources can be loaded. Use the script-src directive to specify allowed domains for script sources and disallow inline scripts ('unsafe-inline'). This prevents the execution of injected scripts.
HTTP-only flag on cookies to prevent client-side scripts from accessing them. This reduces the risk of session hijacking through cookie theft.
Deploy a WAF that includes XSS protection. WAFs can detect and block malicious requests containing XSS payloads, providing an additional layer of defense.
Conduct regular security assessments and penetration testing to identify and address any XSS vulnerabilities. Use automated tools, manual code reviews, and security audits to uncover potential security weaknesses.
How to Find ?
STEP #1: Simple visit any website paste the html injection code in search bar.
STEP #2: Now you can see your search bar is Vulnerable to Reflected Html injection.
How to Report
Hello Team
I'm Prince Pal a white security researcher from Mumbai INDIA, founded Vulnerability on your website: https://www.exmple.com
Vulnerability Name : Reflected Html Injection
Description:
Reflected GET Injection occurs, when our input is being displayed (reflected) on the website. Suppose, we have a simple page with a search form, which is vulnerable to this attack. Then if we would type any HTML code, it will appear on our website and at the same time, it will be injected into the HTML document
Vulnerable URL :
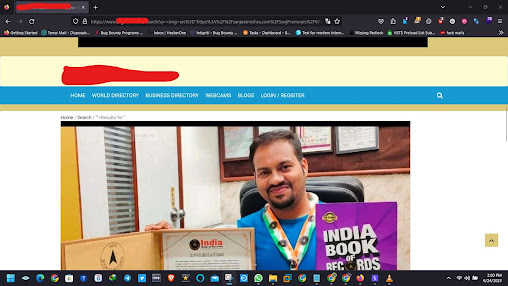
https://www.exmple.com/search?q=%3Cimg+src%3D%22https%3A%2F%2Fsanjeetmishra.com%2FSanjPromopic%2FWhatsApp%2520Image%25202023-05-03%2520at%25207.56.39%2520AM.jpeg%22+alt%3D%22Girl%C2%A0in%C2%A0a%C2%A0jacket%22%3E
Steps to reproduce ?
1.Visit on your website:https://www.exmple.com
2.Simple paste the html payload in the search bar .
payload : <img src="https://sanjeetmishra.com/SanjPromopic/WhatsApp%20Image%202023-05-03%20at%207.56.39%20AM.jpeg" alt="Girl in a jacket">
5.now your website is vulnerable to reflected html injection.6.Please check the POC (Video) For More Information .
Impact: A phony form might be used by the attacker to steal password information saved in the browser or to fool a user into entering their login information. Malicious actors may be granted administrative access to the online application if the targeted user has those rights.
Mitigation :
1. Every input should be checked if it contains any script code or any HTML code. One should check if the code contains any special script or HTML brackets – <script></script>, <html></html>.
2. There are many functions for checking if the code contains any special brackets.
POC: Video & Screenshot
for more details you can ping me on mail
Thanks & Regard,
Prince Pal
Indian Bug Hunter
Payload Account :- paypal.me/Princebughunter



Comments
Post a Comment