Buffer Overflow Attack
Introduction to Buffer Overflow Attack
Buffer overflow is a common vulnerability in computer systems and software applications that can be exploited by attackers. It occurs when a program attempts to store more data in a buffer, a temporary storage area, than it can handle. This extra data can overwrite adjacent memory locations, leading to unpredictable behavior and potentially allowing an attacker to execute malicious code.
When a program is running, it allocates memory for variables and data structures, including buffers. A buffer is a fixed-size storage area designed to hold a specific amount of data.
The program receives input from various sources, such as user input, network packets, or file content. The input is stored in a buffer.
Buffer overflow attacks can have severe consequences, including system crashes, unauthorized access, and the execution of arbitrary code. They are often used to exploit vulnerabilities in software applications, operating systems, or network protocols.
Why is very dangerous buffer overflow attack ?
Buffer overflow attacks can provide attackers with full control over a compromised system. They can escalate their privileges, bypass security mechanisms, and gain access to sensitive information or resources. Once inside the system, attackers can further exploit the compromised environment to launch additional attacks or pivot to other systems within the network.
Buffer overflow attacks can be challenging to detect because they exploit vulnerabilities in the underlying code. They often do not generate obvious signs of compromise or abnormal behavior, making it difficult for traditional security mechanisms to identify the attack. This delay in detection allows attackers to carry out their malicious activities undetected for an extended period, exacerbating the potential damage.
Given the severity of buffer overflow attacks, it is crucial for developers and system administrators to follow secure coding practices, conduct rigorous security testing, and promptly apply patches and updates to mitigate the risk of such vulnerabilities being exploited.
How to prevent ?
Preventing buffer overflow attacks requires a combination of secure coding practices, proper input validation, and robust defensive programming techniques.
Limit the permissions of executable memory regions to prevent the execution of injected shellcode. Data Execution Prevention (DEP) and similar mechanisms can help enforce this restriction.
Implement robust input validation mechanisms to ensure that user-supplied data does not exceed the boundaries of buffers or data structures. Validate input size and enforce proper bounds checking to prevent buffer overflows.
How to Find ?
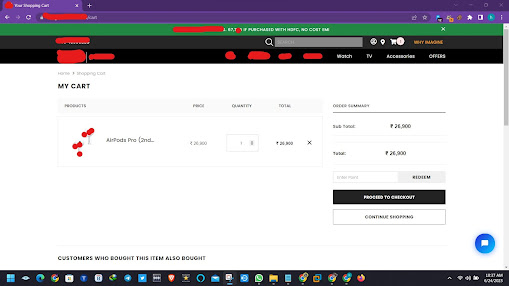
STEP #1: First Visit any site add the any product in add to cart option and go to view cart option .
How to Report ?
I'm Career Technology Cyber Security India a white security researcher from Mumbai INDIA, founded Vulnerability on your website :- https://imagineonline.store/
Vulnerability Name : Buffer Overflow Attack
Summary :
A buffer overflow attack typically involves violating programming languages and overwriting the bounds of the buffers they exist on. Most buffer overflows are caused by the combination of manipulating memory and mistaken assumptions around the composition or size of data.
Steps to reproduce ?
1. Simply visit the URL : https://exmple.com/
2. Follow the options, Click the airpods option > Quick view > Add to cart > View cart
3. Go to the Notepad, Copy the 2700000 Number & paste the Quantity place
4.Then your site is temporary crashed
5.Please check the POC (Video) For More Information's
Impact :
Buffer overflows can affect all types of software. They typically result from malformed inputs or failure to allocate enough space for the buffer. If the transaction overwrites executable code, it can cause the program to behave unpredictably and generate incorrect results, memory access errors, or crashes websites.
Mitigation :
buffer overflow is one of the best known forms of software security vulnerability and is still a commonly used cyber attack. You can prevent a buffer overflow attack by auditing code, providing training, using compiler tools, using safe functions, patching web and application servers, and scanning applications.
PFA of video for steps by steps guidance also help to regenerate the Vulnerability
Thanks & Regard,
Career Technology Cyber Security India
Indian Bug Hunter



Comments
Post a Comment