Reflected Cross-site Scripting
The Beginners Guide to Reflected XSS Vulnerability
Let’s start to details of a Manual User Enumeration vulnerability. We are going to about the basic description of the vulnerability and
In This Article ?
- Introduction to Cross-site scripting
- What is Reflected XSS
- How to find Reflected XSS Vulnerability
- Reflected XSS Prevention
- Why is Reflected XSS Dangerous
Cross-site scripting (XSS) is a type of web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. It occurs when a web application does not properly validate or sanitize user-provided input and includes it in the output sent to other users.
The basic idea behind XSS attacks is to exploit the trust that users have in a particular website. Attackers craft malicious scripts, typically written in JavaScript, and inject them into the vulnerable web application. When other users visit the affected page, their browsers unknowingly execute the injected script, which can lead to various malicious activities.
What is Reflected XSS ?
Reflected XSS is a type of cross-site scripting attack where the malicious script is embedded in a URL or other input and is immediately reflected back to the user by the web application. The term "reflected" refers to the fact that the injected script is not permanently stored on the target server but is rather included in the response generated by the server and sent back to the user.
Reflected XSS attacks often rely on social engineering techniques to trick users into clicking on a malicious link or visiting a compromised website. For example, an attacker might send phishing emails with a link to a legitimate-looking website that includes the crafted URL containing the malicious script. When the victim clicks on the link, the script is executed in their browser.
How to Find Reflected XSS Vulnerability ?
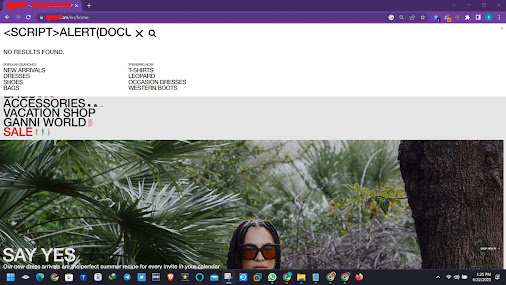
STEP #1: Go to any site and inject this payload <script>alert("open bug bounty")</script> in the search bar.
That was a payload but you want to use a many xss payload e.g: https://github.com/payloadbox/xss-payload-list and you can search many bugs .
Mark session cookies as "HTTP-only" to prevent JavaScript access. This helps mitigate the risk of cookie theft through XSS attacks.
Set appropriate security headers in the HTTP response, such as the "X-XSS-Protection" header, which enables the browser's built-in XSS protection mechanisms.
Implement strict input validation on both the client and server sides to ensure that user-supplied data is properly validated and sanitized. This includes validating the data type, length, and format, as well as using whitelisting or blacklisting techniques to filter out potentially malicious input.
Always encode user-generated or dynamic content before including it in the HTML output. HTML entity encoding, such as converting special characters to their corresponding HTML entities, can prevent malicious code from being interpreted by the browser.



Comments
Post a Comment