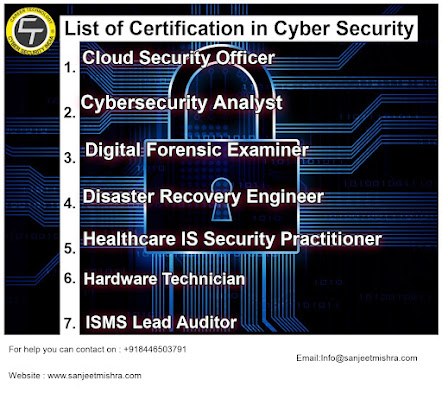
List of Certification in Cyber Security
List of Certification in Cyber Security
What is cloud security certification?
Certificate of Cloud Security Knowledge (CCSK)
This cloud security credential from the Cloud Security Alliance (CSA) covers a range of key cloud security issues that can empower you to tailor security solutions in a cloud environment. Topics covered include: Cloud architecture. Governance, risk management, legal issues.
what is Cybersecurity Analyst?
A cyber security analyst is primarily responsible for protecting a company's network and systems from cyber attacks. This involves researching upcoming IT trends, creating contingency plans, reviewing suspicious activities, reporting security breaches, and educating the rest of the company on security measures.
What does a digital forensics person do?
What do computer forensics analysts do? Digital forensics analysts mainly work to retrieve, catalog, and safeguard digital data related to cybercrime investigations. They also preserve evidence to ensure its admissibility in court. They may also advise other investigators about the value of digital evidence
What do you do in disaster recovery?
A disaster recovery (DR) plan is a formal document created by an organization that contains detailed instructions on how to respond to unplanned incidents such as natural disasters, power outages, cyber attacks and any other disruptive events.
Being a Disaster Recovery Engineer (DRE) validates that you are prepared to work with businesses to create and implement disaster recovery and business continuity plans.
What is Healthcare IS Security Practitioner?
A HealthCare Information Security and Privacy Practitioner (HCISPP) is a professional who has earned a certification from the International Information Systems Security Certification Consortium (ISC2) which identifies them as having expertise in key areas of knowledge regarding healthcare information, security
What is the job of hardware technician?
Hardware Technicians support and maintain computer systems and peripherals by installing, configuring, testing, troubleshooting, and repairing hardware. You need extensive experience, or a formal qualification in information technology to work as a Hardware Technician.
The Hardware Technician's role is to support and maintain in-house technology equipment and IT assets. This includes installing, configuring, diagnosing, repairing, and upgrading all County hardware and equipment while ensuring its optimal performance.
What is ISMS Lead Auditor?
Auditors seeking to perform and lead Information Security Management System (ISMS) certification audits. Managers or consultants seeking to master an Information Security Management System audit process. Individuals responsible for maintaining conformance with Information Security Management System requirements.
For help you can contact on : +918446503791
Email : Info@sanjeetmishra.com
Website : www.sanjeetmishra.com


Comments
Post a Comment