Incident Response for IoT & OT Environments

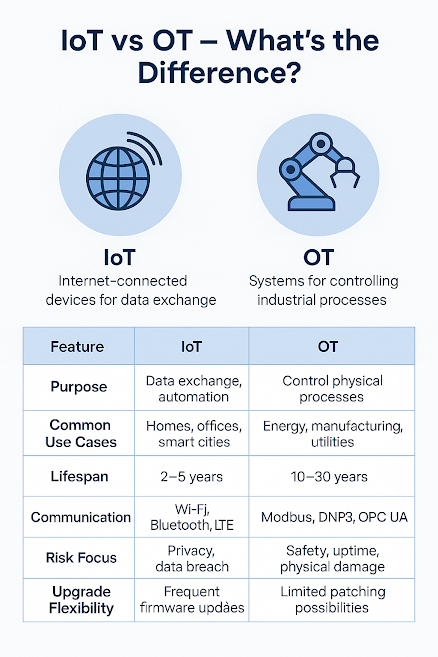
When cyber threats hit industrial systems, fast and smart action is key. That’s where a strong Incident Response (IR) plan comes in tailored for the unique risks of IoT and OT. Why Incident Response Matters? Unlike IT, OT incidents can cause: Equipment failure Production downtime Physical harm or safety issues Being prepared means minimizing damage and recovery time. Key IR Steps for IoT/OT Preparation Create an IR playbook specific to OT systems Define roles across IT + OT teams Detection & Analysis Use network monitoring tools Look for anomalies in PLCs, SCADA, sensors Containment Isolate infected zones Avoid halting critical processes unless needed Eradication & Recovery Remove malware Restore from backups Validate system integrity Post-Incident Review Update playbooks Share lessons with teams Best Practices Run joint IT/OT tabletop exercises Use cyber-physical simulators for training Keep b...